USE CASE
In recent years, Microsoft Azure became a very popular cloud technology to many customers to host their workloads. As a result, extending the SD-WAN fabric became essential to connect to the workloads in the Azure cloud. This blog post will cover how to leverage the Meraki SD-WAN fabric to connect to the Azure cloud and run BGP routing protocol to exchange routes between your Azure VNET(s) and the Meraki Site-to-Site VPN network.
IMPLEMENTATION
The first step is to build Meraki vMX in the Azure cloud.
-
Create Resource Group. Choose any name and region
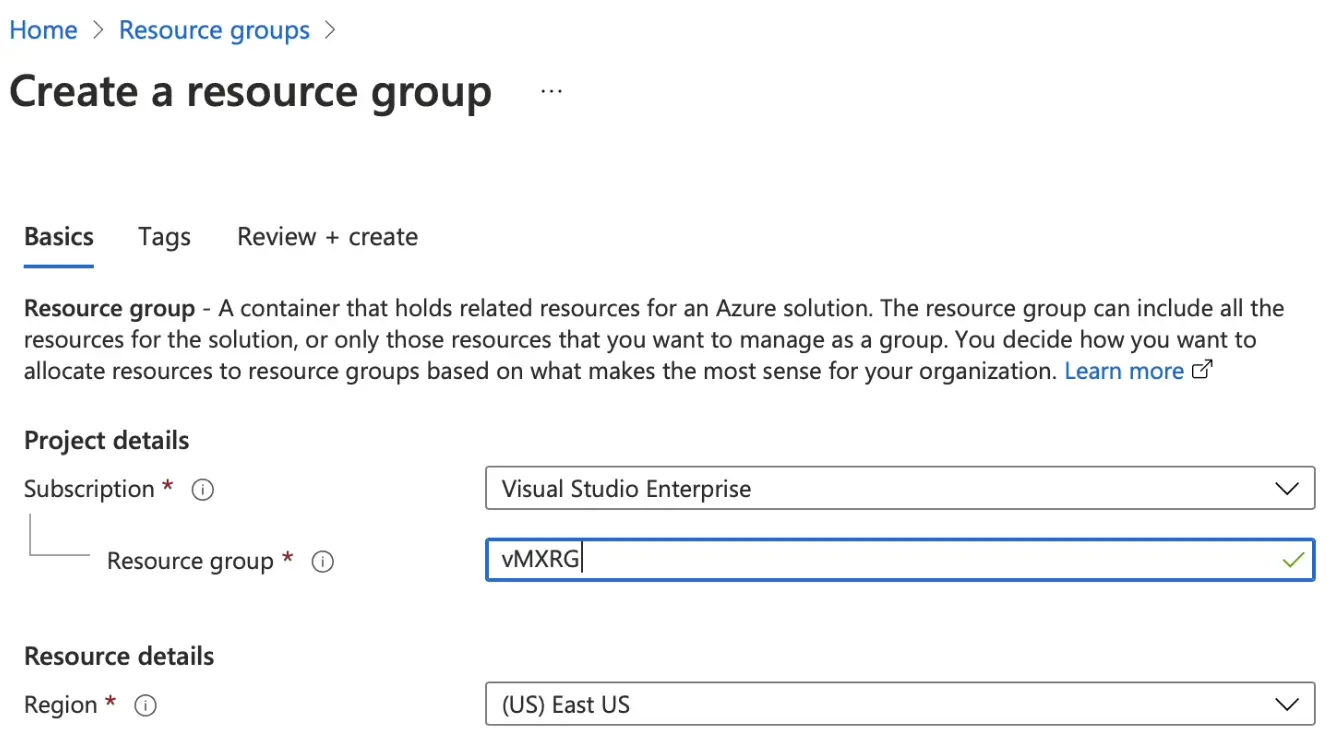
-
Create vNET/subnet and attach them to the resource group created in step 1.
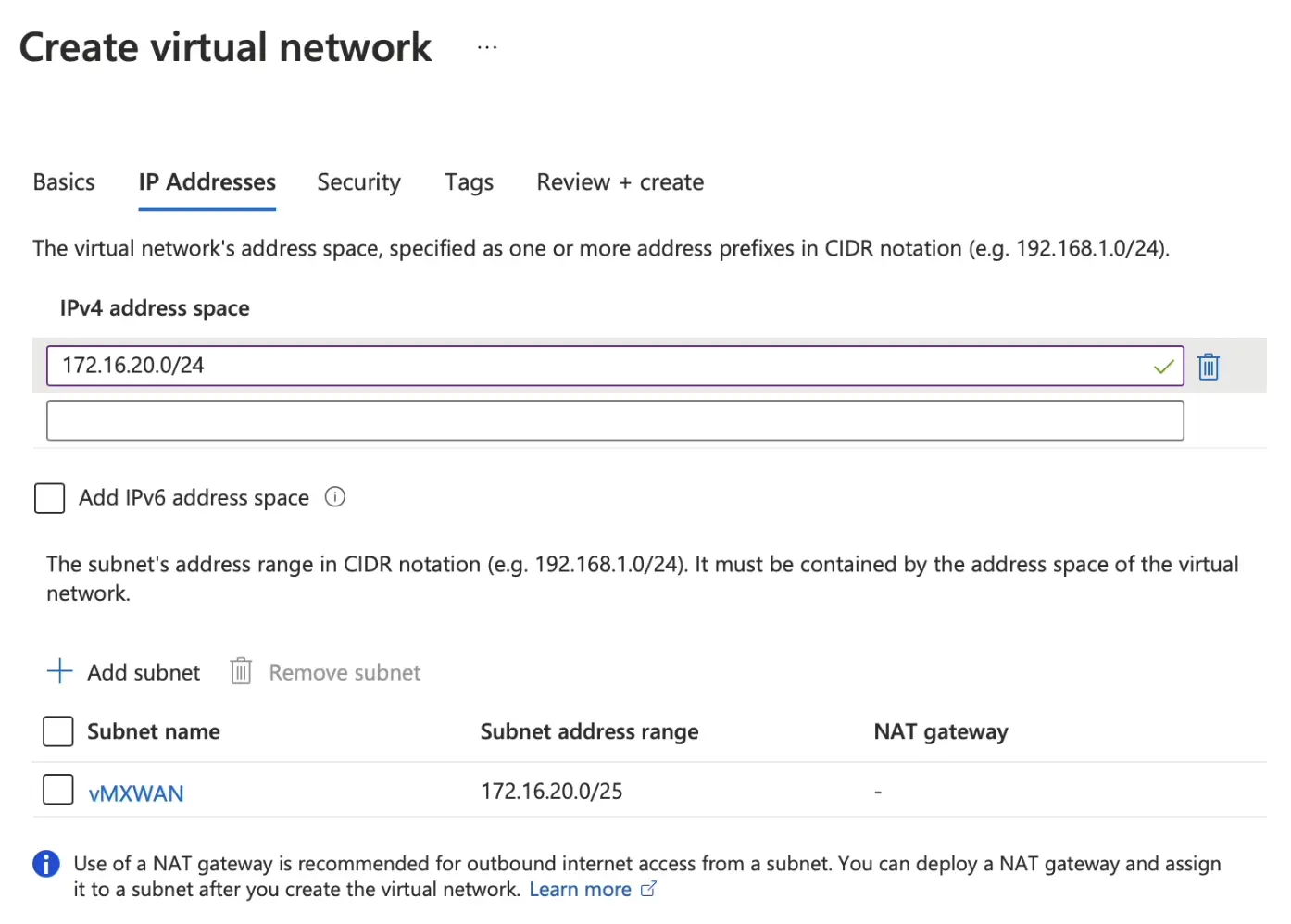
-
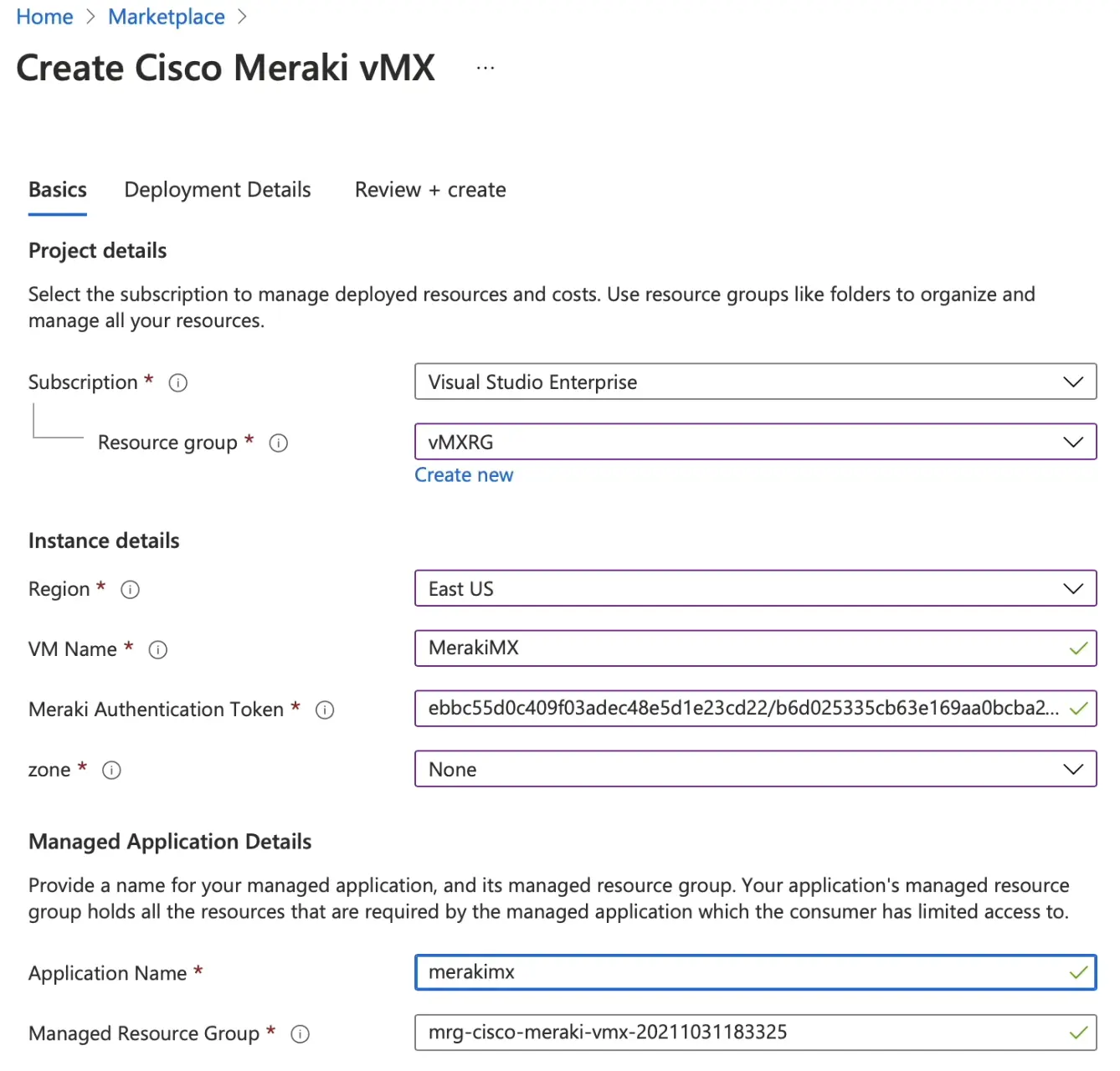
From Azure Marketplace, search for Cisco Meraki vMX, then Click on Create.
-
Select the resource group that we created in step 1 and select the same region.
-
Attach the vNET to the vMX.
-
From Meraki Dashboard, create a new network with a security appliance. Then, click on Add vMX. Next, click on generate authentication token and copy the field and paste it into the Azure.
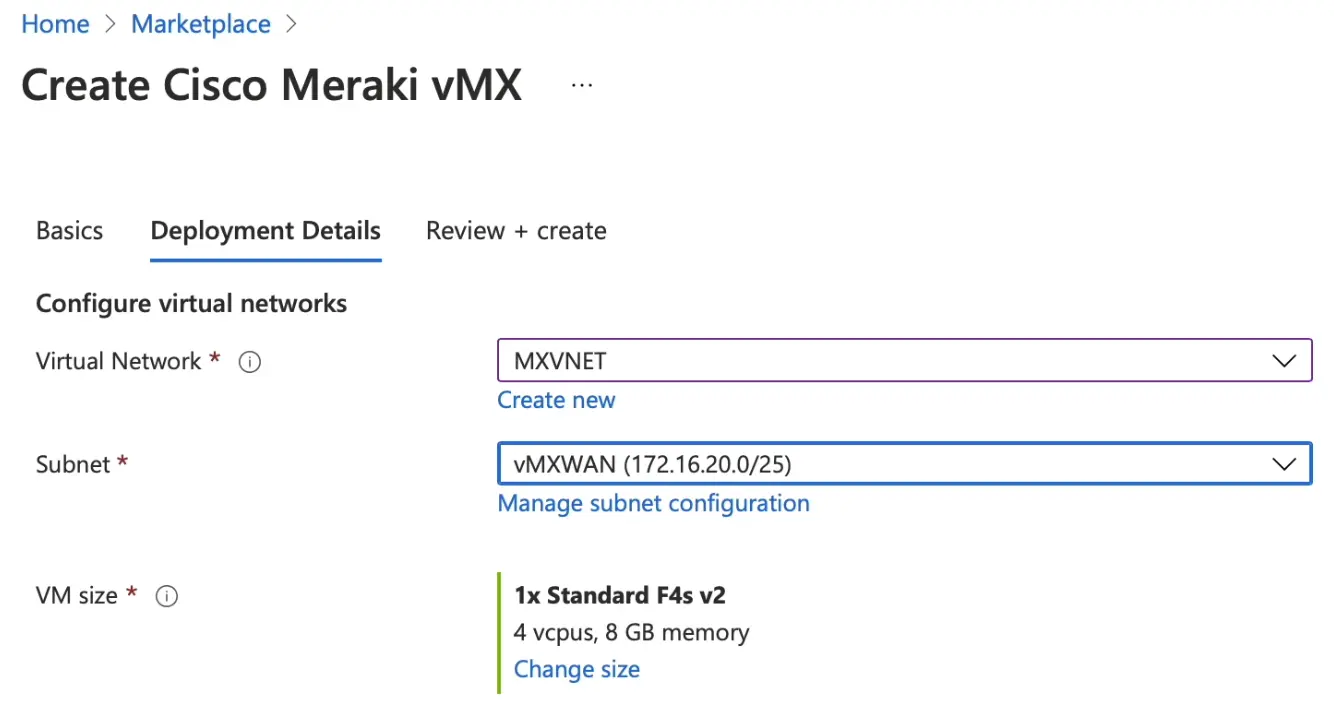
The second step is to build Azure Route Server
-
Route Servers need a range with specific name to be created - "RouteServerSubnet" and needs to be at least /27 range. This new subnet will be part of vMX VNET.
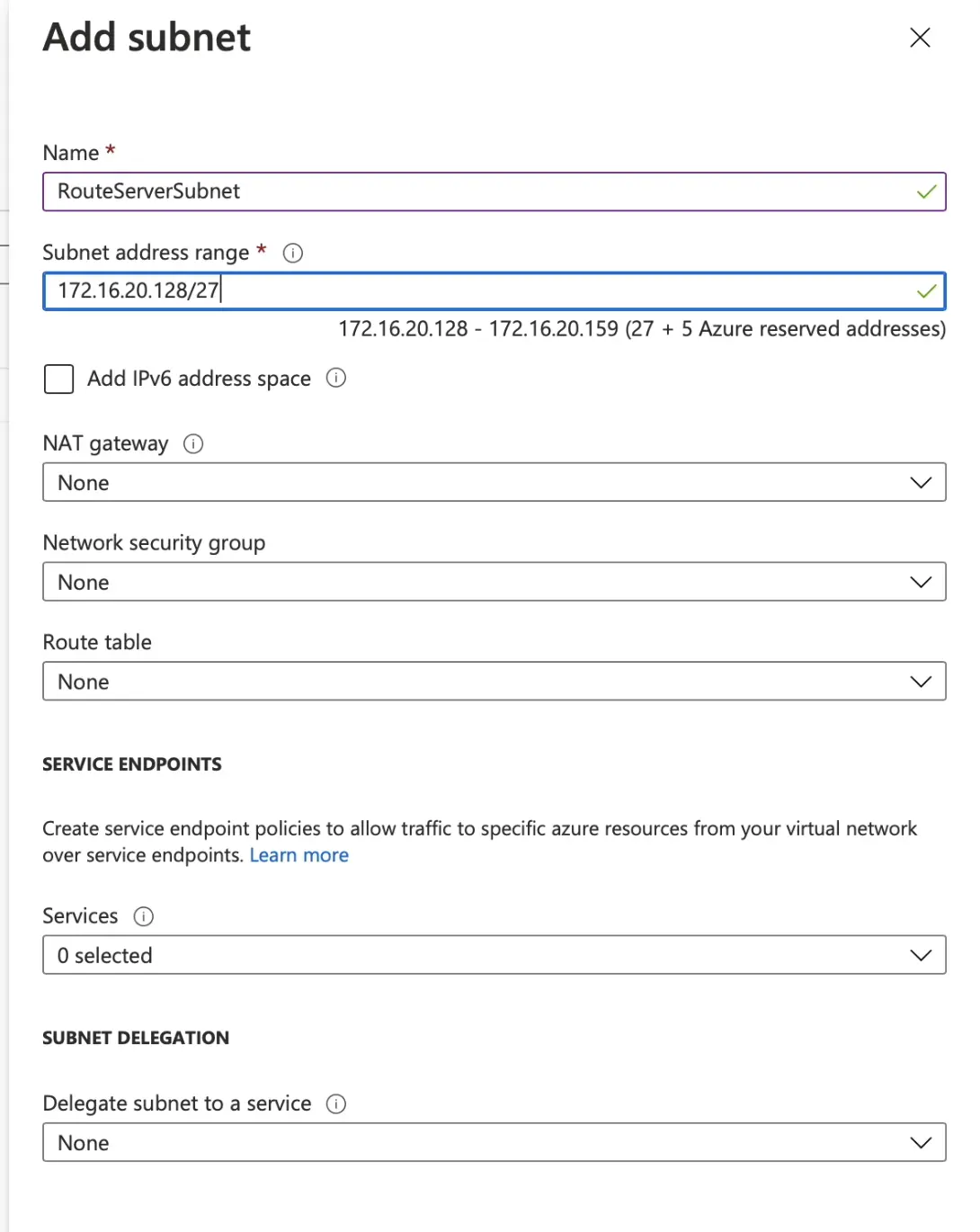
-
From main menu select/search for Route Servers then create a route server and attach it to the same Resource Group as the vMX.
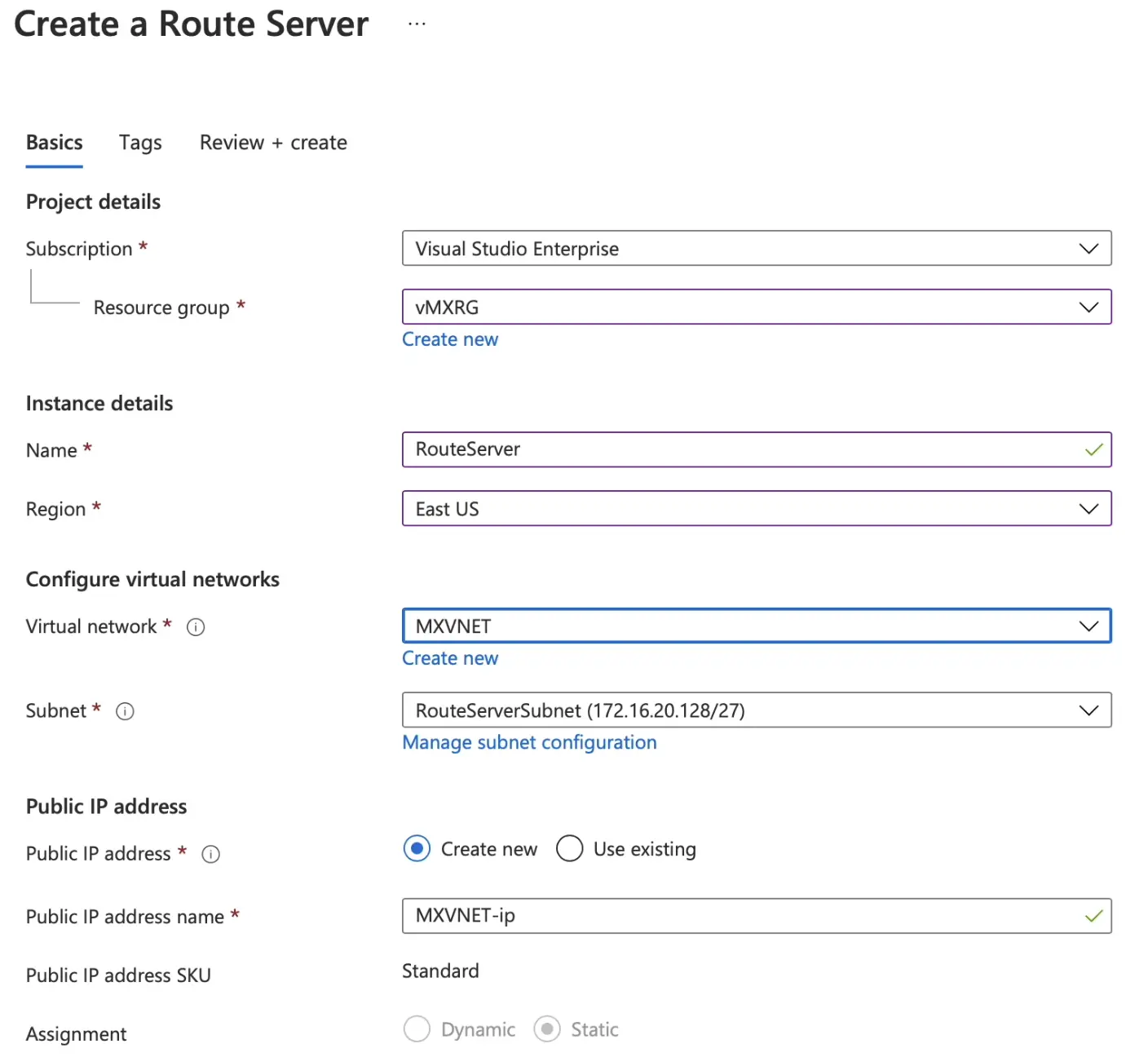
-
Click on the route server that we just created and keep note of the ASN number and the BGP Peer IPs.
-
Then from the left hand side menu, choose Peers then add a peer.
-
Configure the details of Meraki vMX. -- Note, There are a range of BGP ASN number reserved by Azure, so make sure to select one out of the ranges
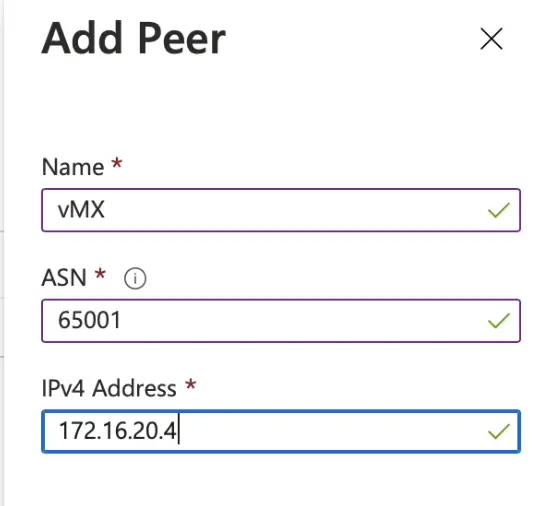
-
After adding the peer, make sure to enable Branch-to-Branch communication by going to Configuration menu under the Route server/Settings section.
The last step is configure Meraki BGP and test
-
From Meraki dashboard, go to Site-to-Site VPN menu and enable the feature (Hub).
-
Then enable BGP and plug in the ASN and IPs you saved in the pervious step.
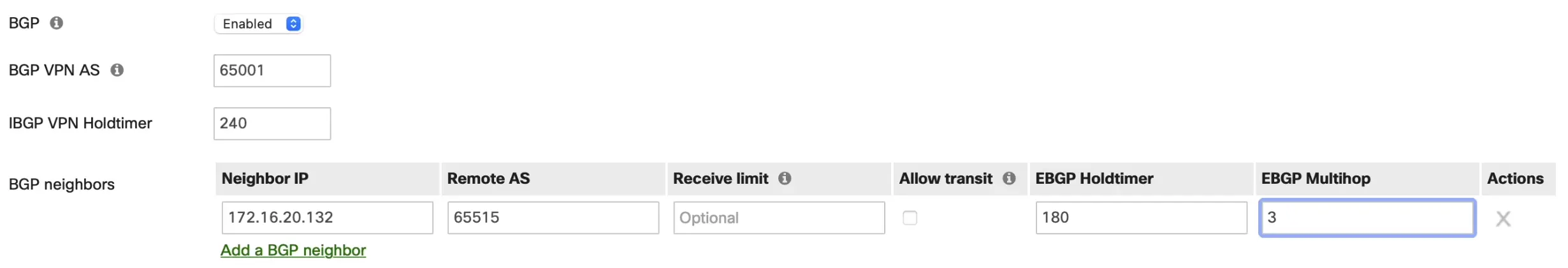
-
From main menu select/search for Route Servers then create a route server and attach it to the same Resource Group as the vMX.
-
Check the Meraki Route table of the vMX to confirm you are getting the Azure routes via BGP. -- Note, below is an example from a spoke route table and its clear that it recieves Azure routes via iBGP from vMX.
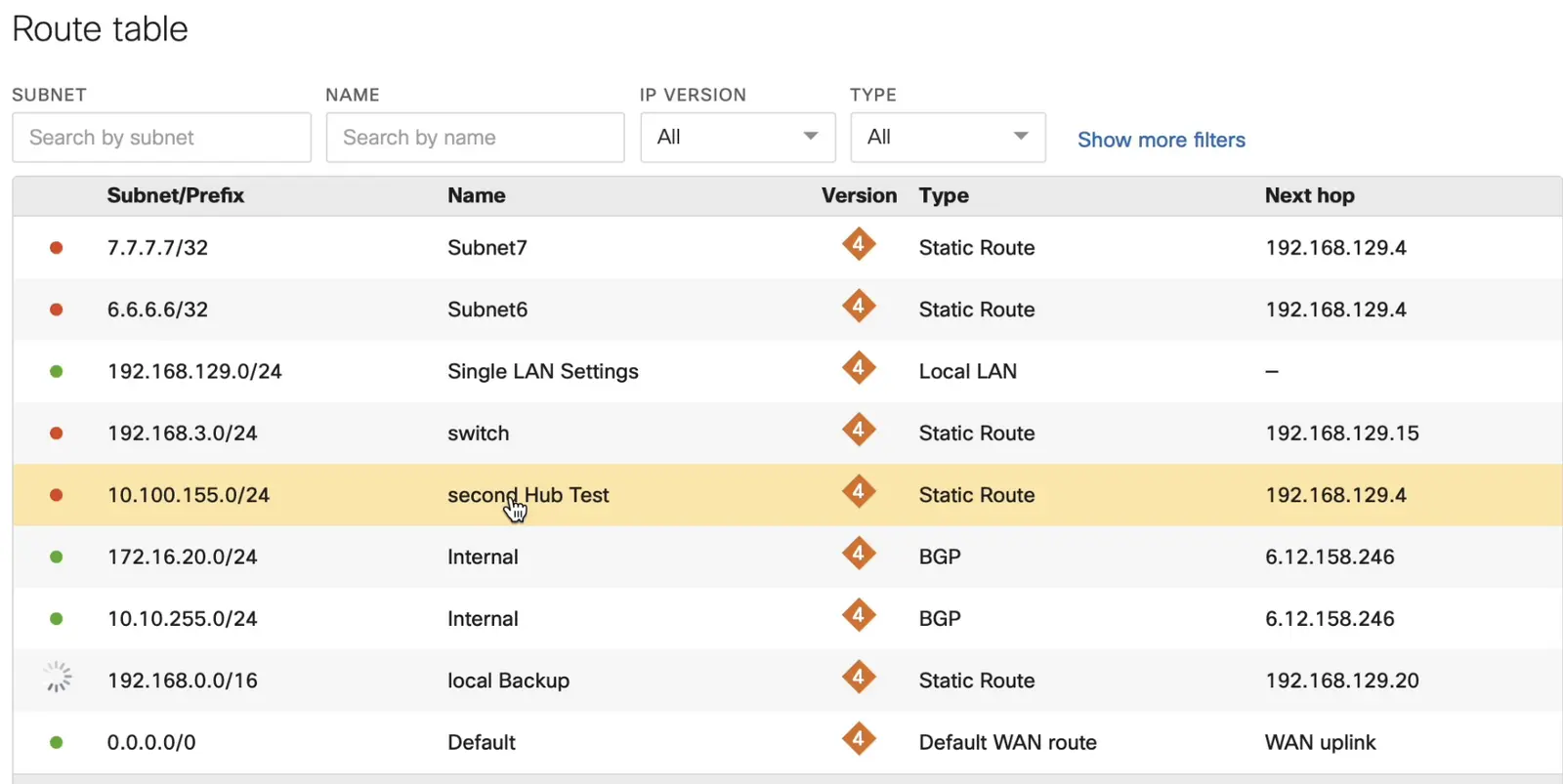
SUMMARY
- Build a new Resource Group in Azure and don't use the one which is built automatically when you deploy Meraki vMX (as its locked).
- Recommended to use new subnet for the vMX.
- Create another /27 subnet with name of "RouteServerSubnet".
- Don't forget to generate a new authentication Token from Meraki Dashboard.
- Configure BGP in Azure and vMX.
- Test the routes.

